Endpoint Security Protection
BCS365 Solutions
SECURE YOUR ENDPOINTS WITH OUR INTEGRATED AND AUTOMATED ENDPOINT SECURITY PROTECTION PACKAGE.
ServiceNow Security Incident Response transforms the standard approach to IT Security investigation, response, and recovery, by applying advanced automation capabilities and centralizing security operations data, insights, and reporting on a single platform.

What's Included?
BCS365 24/7/365 Security Desk
Next Gen AV, Endpoint Detection and Response, Threat Intelligence: Get protection across the entire threat lifecycle by combining machine learning, artificial intelligence, behavioral analytics and proactive threat hunting, all in a single solution.
Phishing, Malware and Ransomware Protection: Phishing, Malware & Ransomware Protection Powerful filtering, using the Internet’s own infrastructure. Block malicious and unwanted domains, IP addresses, and cloud applications before a connection is ever established.
Integrated Suite of Security Products: Our program offers an integrated suite of advanced security products to safeguard your email communications. From robust firewalls to sophisticated encryption tools, we provide a comprehensive solution to protect your sensitive information.
Prioritization of Security: We prioritize the security of your email communications above all else. Our program ensures that potential threats are swiftly identified and addressed, minimizing the risk of data breaches and ensuring business continuity.
Utilization of Threat Intelligence: By leveraging advanced threat intelligence, we stay one step ahead of cyber threats. Our program utilizes real-time data and analysis to proactively detect and respond to potential security incidents.
Rapid Response and Actions: In the event of a security incident, our expert team is ready to take immediate action. We swiftly analyze the situation, assess the impact, and implement the necessary measures to neutralize the threat, ensuring minimal disruption to your business operations.
Threat Remediation: Our program goes beyond incident response. We work closely with your organization to eliminate vulnerabilities and strengthen your overall security posture. By addressing the root causes, we help prevent future incidents and enhance your security resilience.
Review of Post-Incident Reports: Learning from past incidents is crucial for continuous improvement. Our program includes a thorough review of post-incident reports, allowing us to identify areas for enhancement and strengthen your security infrastructure.
NIST INCIDENT RESPONSE
A DRILLDOWN ON FRAMEWORK:
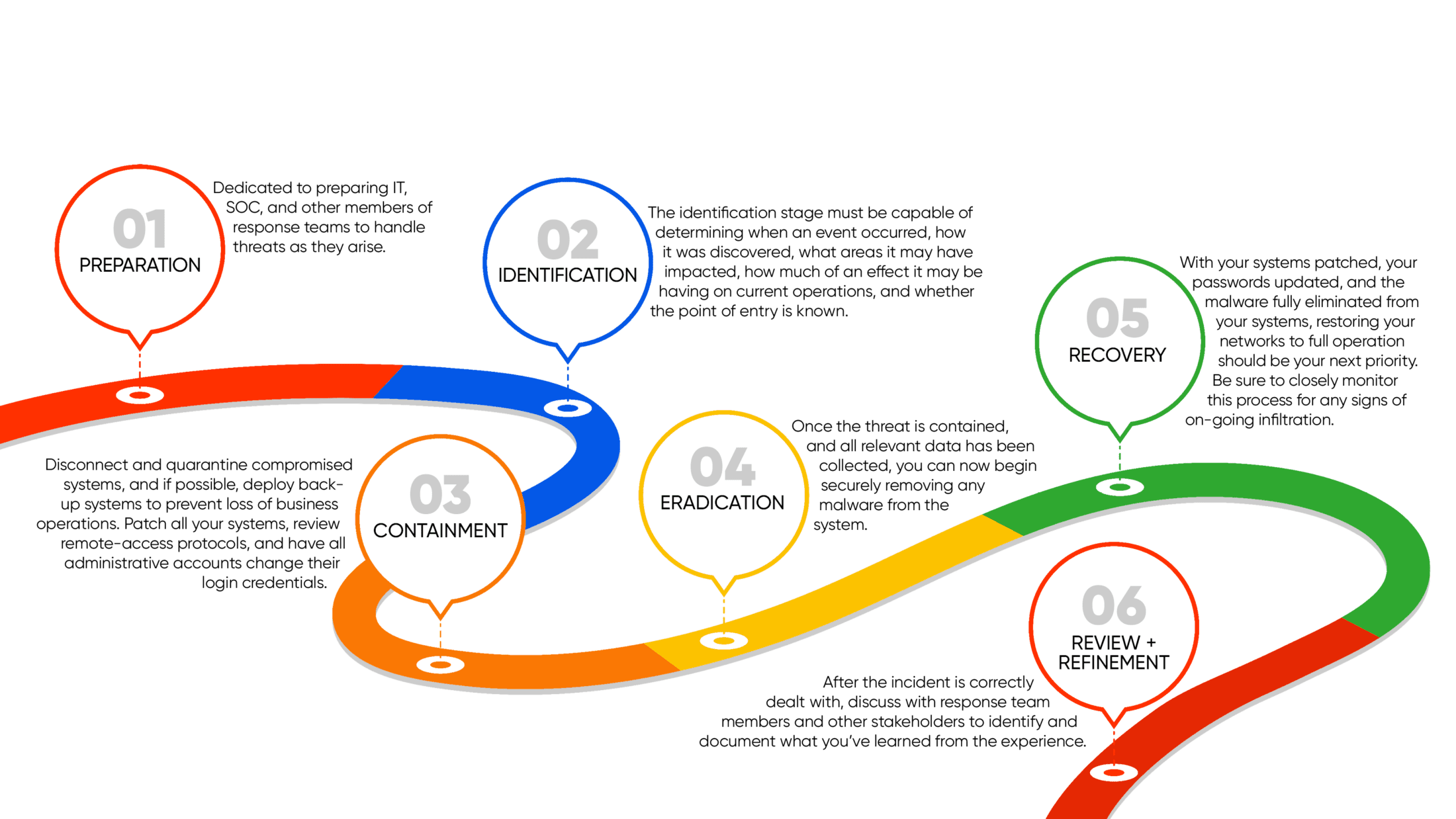
ADDITIONAL BENEFITS:
Simplifies your security stack and deploys in record time while using crowdsourced data and cloud analytics to stop advanced threats.
Protects with the power of big data and AI to provide instant visibility and protection across the entire threat lifecycle.
Unifies next generation antivirus (NGAV), endpoint detection and response (EDR), device control, vulnerability assessment and IT hygiene with a single, cloud-delivered solution.
Delivers next-generation endpoint protection to detect adversaries, eject them quickly and keep them out.
Automates protection against both known and emergent threats by analyzing a cross-section of Internet activity to observe staged attacks before they are launched.
Extends the DNS by incorporating features such as content filtering and phishing protection.
How We Do It:
UEBA
UEBA, which stands for User Entity Behavior Analytics, utilizes machine learning to scrutinize raw data, produce behavior profiles, and identify irregular behavior. This helps in recognizing advanced attacks, thus improving the overall security system.
MITRE ATTACK
Mitre Attack is a framework that provides advanced detection policies, which can detect incidents in real-time. It offers a comprehensive and structured approach to detecting, responding to, and recovering
from cyber-attacks.
CUSTOM DETECTION POLICIES
Custom detection policies designed by BCS365 can be used to alert on specific events that matter the most to the user. For instance, alerts can be generated when users are added to sensitive groups, signins are made from unapproved countries, or users access specific SharePoint sites.
ALERT AGGREGATION
Alert aggregation is an essential process that collects alerts from all areas of the Microsoft tenant. This ensures that all alerts are reviewed with the necessary urgency, thus preventing any potential security breaches.
.png)