- Services
- Cybersecurity
- Endpoint Data Loss Protection (EDLP)
- Managed Detection & Response (MDR)
- Identity Threat Detection & Response (ITDR)
- Enterprise Network Security
- Cybersecurity Awareness Training
- Risk Assessment and Penetration Testing
- Incident Response
- Data Protection
- Vulnerability Management
- Managed Email Security
- Microsoft 365 ITDR
- Managed IT Services
- Cloud
- Telepresence and Video Conferencing
- Physical Security
- Network Cabling
- DevOps
- Managed Compliance
- Cybersecurity
- Industries
- Insights
- Case Studies
- About BCS365
- Contact
- Customer Portal
- Schedule a Consultation
- Services
- Cybersecurity
- Endpoint Data Loss protection (EDLP)
- Managed Detection & Response (MDR)
- Identity Threat Detection & Response (IDTR)
- Enterprise Network Security
- Cybersecurity Awareness Training
- Risk Assessment and Penetration Testing
- Incident Response
- Data Protection
- Vulnerability Management
- Managed Email Security
- Microsoft 365 ITDR
- Managed IT Services
- Cloud
- Telepresence and Video Conferencing
- Physical Security
- Network Cabling
- DevOps Services
- Managed Compliance
- Cybersecurity
- Industries
- Insights
- Case Studies
- About BCS365
- Careers
- Contact
- Support
Email is the most common attack vector for malware, with around 35% of malware delivered via email in 2023.
PROTECT YOUR BUSINESS WITH OUR COMPREHENSIVE EMAIL SECURITY PROGRAM
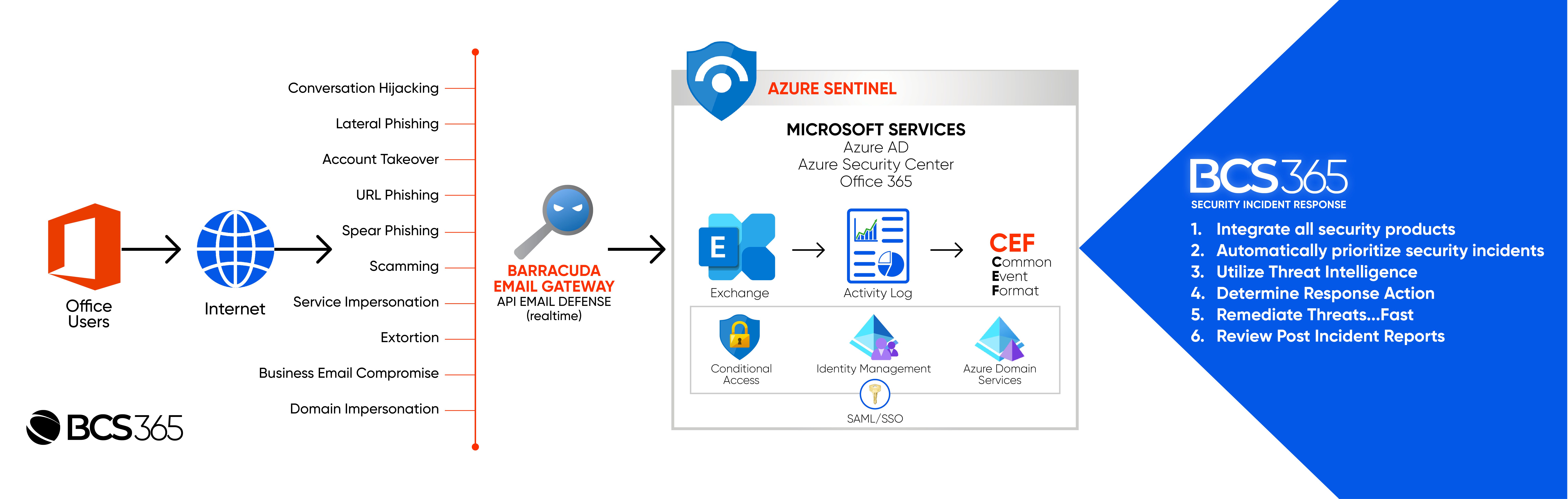
By outsourcing the management of email security to BCS365, you can ensure that your sensitive data remains secure and confidential. Our managed email security program offers comprehensive protection against phishing attempts, malware infections, spam emails, and other malicious activities.
Our 24/7/365 managed services provide round-the-clock monitoring and threat protection capabilities. This means that any suspicious activity or potential breach can be identified and addressed in real-time, minimizing the risk of data loss or unauthorized access.
What's Included?
How We Do It
UEBA
User Entity Behavior Analytics uses machine learning to scrutinize raw data, produce behavior profiles, & identify irregular behavior. This helps in recognizing advanced attacks.
MITRE ATTACK
A framework that provides advanced detection policies, which can detect incidents in real-time, offering A structured approach to detecting, responding to, & recovering
from cyber-attacks.
CUSTOM DETECTION
BCS365's custom detection policies alert users to key events, such as adding users to sensitive groups, sign-ins from unapproved countries, or accessing specific SharePoint sites.
ALERT AGGREGATION
An essential process that collects alerts from all areas of the Microsoft tenant. This ensures that all alerts are reviewed with the necessary urgency, thus preventing any potential security breaches.


